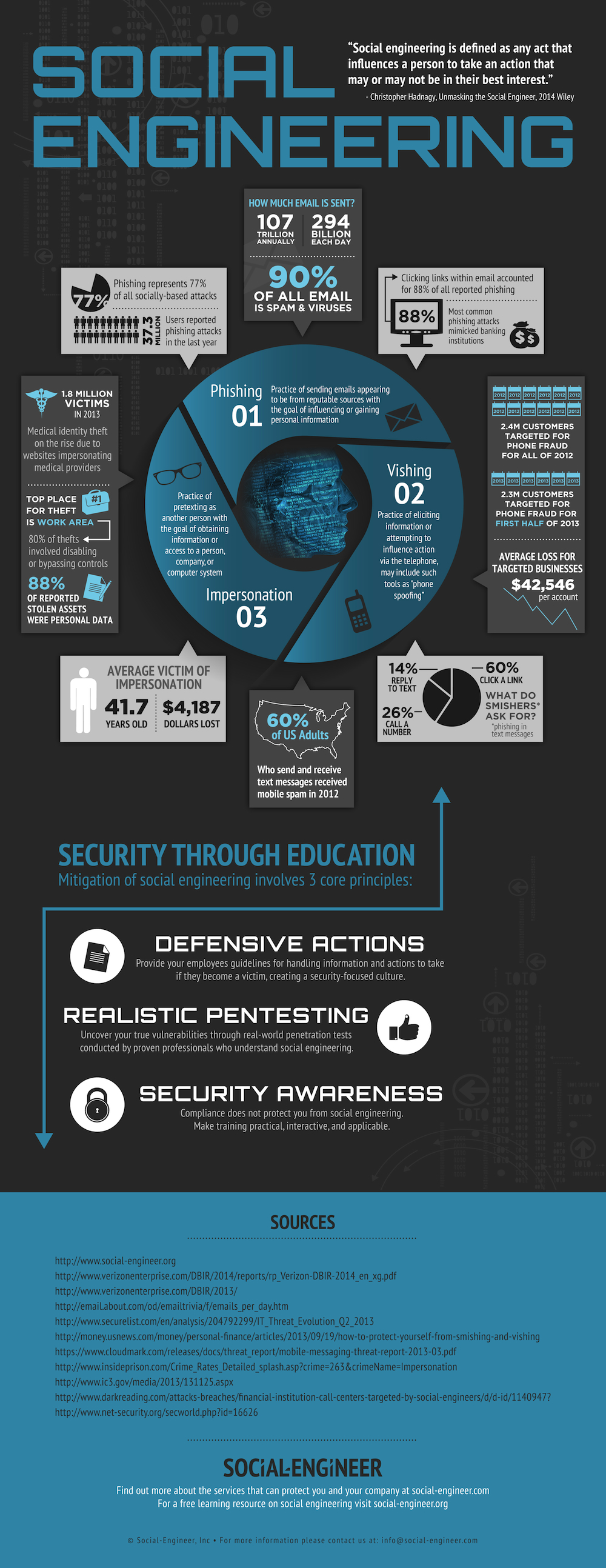
Social engineering
Attacks could be divided into two categories based on the way how the attack works. Passive attacks are attacks that do not modify the information or the system. Such attacks are mainly used for gathering information. Active attacks try to get access to the system so that it would be possible to affect or modify it. Thus, wiretapping is considered a passive attack if the information is not altered due to wiretapping. However, using malware or exploiting vulnerabilities to breach/infect computer networks is an active attack method.
When people read about attacks against computer systems or data breaches, they often think that the attacker was an evil hacker who used malicious programs or sophisticated tools to breach the systems or leak the data. This assumption might not be correct as the attacker looks for the weakest link in the system when planning the attack, and usually, the weakest link is the human. Thus, many attacks are designed to abuse psychological weaknesses to gain access to information or computer systems. Attacks against human weaknesses do not require sophisticated tools and are cheap to implement. Such attacks are classified with the term social engineering.
Social engineering techniques
Social engineering uses human weaknesses to get access to the desired resources. The attacker might use social engineering to get direct access to the resources, e.g., by using an employee to infect the company's internal network. However, the attacker might also indirectly access the resources if the employee gives out confidential information. One might think that it is difficult to get an employee to trust a stranger, and therefore, such attacks would be unlikely, but unfortunately, this is not true. A good social engineer starts by going through all the background information about the company and its employees to find a suitable pretext or find a weak spot in the system.
Gathering information about the target
The attacker needs as much information about the target as possible. It is probably important to know the inner structure of the organisation and the details about how the organisation operates. In addition, it would be beneficial to know which kind of software is used by the organisation and which security measures are used. So, how could the attacker get access to such information?
First, all legally available information will be gathered. Probably the website of the organisation gives some helpful information to the attacker. Still, much more information could be found by using search engines as they might store cached information that can not be directly accessed anymore. In addition, the employees might leak information about the employer in blogs or social media. It might also be possible to apply for a job in the organisation to gather additional information during the job interview.
When the initial research is done, the attacker could start to use illegal means to gather information. It might be possible to follow an employee of the targeted organisation to collect data from phone calls or conversations. It might be possible to gather essential details just by sitting next to the targeted employee in a restaurant. Another option for the attacker is to pretend to be someone else to gain more information about the target. However, much more information could be gathered if the attacker could enter the areas of the organisation that are restricted to the public. One way to get into the restricted areas is to use tailgating, i.e., to follow someone through the door. Tailgating is not allowed in many companies, and this means that the employees that enter the restricted area always have to use their ID. Shoulder surfing might also work, i.e., once the attacker can enter the facilities, it might be possible to walk around and see what can be seen from the employees' screens. A good place for finding information is the dumpster of the organisation that is being targeted. This method is called dumpster diving, which is why many companies lock their dumpsters.
Analyzing the gathered information to find a weak spot
Once the attacker has enough information about the target, it is possible to plan the actual attack. The goal of an attacker might be to access some classified information or to infect a computer in the internal network to gain remote access. The weak point might be an employee that could be manipulated using the gathered information. However, it might be possible that the attacker has collected enough information to access the facilities to infect the internal network. For example, some companies may be less strict about checking couriers and people who do maintenance related work.
Implementing the attack
The attack might be made remotely over the phone or email by using the gathered information to manipulate the employees. For example, one might call an employee pretending to be from the IT service and ask them to reveal information about the software or even reveal the password. Specially crafted emails could be used to gather confidential information from the employees or to infect their computers. The attacker may infect the employee's computer by creating a malicious web page and tricking the employee into clicking on the link in an innocent-looking email. An easily usable trick that helps to infect the company network is to drop an infected USB stick near the organisation such that the employees would find the USB stick. The USB stick might contain files like salaries_2022.xls that trick the employees into opening the infected files in their computers.
- Concerns about USB security are real: 48% of people do plug-in USB drives found in parking lots.
- BAD USB

A good overview of social engineering techniques, information gathering, psychological principles and attack vectors can be found from The Social Engineering Framework.
Some real-life examples of social engineering:
- A Twitter account was hijacked by using social engineering against PayPal and GoDaddy
- How Apple and Amazon Security Flaws Led to My Epic Hacking
How to protect yourself or the employees from social engineering
The critical factor in avoiding damage by social engineering is the awareness of the employees. There are no security features that can protect the employee from social engineering if they do not know what social engineering is and how it is used. Therefore, the employees have to be trained to notice suspicious behaviour.
In addition, the organisation has to have a good security policy that specifies how the employees have to act in certain situations. Should the employees give the delivery man or service personnel access to the building, and how should they determine that the person is who he/she claims to be. The security policy also has to state who has the responsibilities and who should be contacted if something suspicious happens.
Phishing
In case of a phishing attack, the attacker tries to win his victim's trust to make the victim do what he wants: either click on a link, download some malicious software or give out information.

Phishing attack in Dilbert comic. (source)
Phishing methods:
- Sending an e-mail with a text that persuades the receiver to click on a link in that e-mail. Such links may look like belonging to a regular service: https://www.your-bank.com/, but in reality take the victim to a page controlled by the attacker. This web page may try to install malware by using potential web browser's vulnerabilities.
- Also, changing the order of subdomain in a web page address is a standard method for misguiding users. For example, a web page at www.ut.courses.ee would probably not be controlled by the University of Tartu but rather by someone managing the courses.ee second-level domain. Remember that subdomain names are to the left of the second-level domain name. Going from left to right means going up in the domain name hierarchy until reaching the top-level domain (com, eu, ee, ...).
- Several tricks are based on text encoding. For example, it is possible to reverse the text order by using a special Unicode symbol (u202e) created for Arabic / Hebrew. Also, some letters in different encodings appear very similar to the letters in the Latin alphabet, but it is another letter for the computer. Such an attack was described in the following blog post: Phishing with Unicode Domains.
Example: crimea_xcod.exe
- If the attack targets a specific victim (called spear-phishing), the attacker may first perform a background search on the intended victim to choose the suitable attack vector or gather information for the pretext.
Examples from Estonia
Phishing attacks are also used in Estonia. The 2013 report by Estonian Information System Authority it was written that phishing emails were used to attack the employees of Elisa, Elion, Estonian University of Life Sciences, University of Tartu and EENet. The quality and quantity of phishing attacks has increased as reported by the corresponding reports for the following years 2014, 2015, 2017. However, the RIA report for 2018 mentioned that: "– for example, we have worked with our partners and Estonian service providers to quickly detect and take down phishing websites. As a result, the number of successful phishing incidents in Estonia has decreased significantly." Still, the usage of phishing has increased according to the RIA reports for 2021, report for 2022, report for 2023, and report for 2024.
Recent phishing attacks
- The employees and students of the University of Tartu get emails that state that the university mailbox is starting to get full, and one has to either connect the IT service or log in to the mailbox to solve the problem. However, the trick is that a link is given to a fake website that looks like the real university mailbox. In addition, such mails might contain the request to send the username and password of the account to the fake IT service. Most of these emails used to be machine-translated, which meant that they contained many mistakes, but recently some phishing emails have appeared that are written in correct Estonian.
- In 2014, people got phone calls from someone who claimed to work for Microsoft. The attacker instructed the victims to install special software (malware) to increase their security.
- Phishing attacks have been used to ask for money. One popular method is to hijack a mail account and then contact the friends or family of the account owner and tell them that an accident has happened and, therefore, some money has to be transferred to the given account. This attack method could work well for people whose children live abroad.
- Example about the misuse of Google ads: Kraken Phishing Warning.
- How Hackers Broke Into John Podesta and Colin Powell’s Gmail Accounts
- In January 2015, an email was sent by someone who claimed to be from the Estonian Tax and Customs Board. The email contained information on the tax returns and asked to navigate to the linked webpage to fill in the tax returns form. The email itself was not written in correct Estonian, but the fake website looked almost like the actual website of the Estonian Tax and Customs Board. However, the URL of the website was different and also, the website contained a form that asked for the credit card number to get the tax return. The fake website can be seen from the following screenshot.
- Fraudsters Used AI to Mimic CEO’s Voice in Unusual Cybercrime Case (2019)

Further reading
- Social engineering framework
- Social engineering
- Real-life examples of social engineering
- How Apple and Amazon Security Flaws Led to My Epic Hacking
- How I Lost My $50,000 Twitter Username
- US Government Agency Compromised by Social Engineering
- How Hackers Broke Into John Podesta and Colin Powell’s Gmail Accounts (2016)
- 2016 Presidential Campaign Hacking Fast Facts
- Fraudsters Used AI to Mimic CEO’s Voice in Unusual Cybercrime Case (2019)
- Hackers Convinced Twitter Employee to Help Them Hijack Accounts (2020)