Blockchain, Bitcoin and payment methods
Blockchain and its applications
Blockchain (in Estonian: plokiahel) is a data structure that consists of several subsequent data blocks that are connected to each other. Data block consists of entries, but their semantics depend on the application of the blockchain in question. The most well-known blockchain application is the cryptocurrency, where data block entries represent users' account balance and/or digitally signed transactions. Such blockchain is usually implemented as a distributed ledger.
To protect blockchain's integrity, each data block contains a hash of the previous block. These hash values link subsequent data blocks together so that modifying the chain (adding or removing data blocks to/from the middle) becomes difficult. The integrity of these hash values, i.e. the blockchain state, is protected by one of the following methods:
- time-stamping the hash values -- periodically publishing the hash values (e.g. in a newspaper)
- digitally signing data blocks (their hash values) by trusted parties.
- rules enforced on the structure of the data blocks that are easily verified but make creating new data blocks computationally difficult and thus also difficult to modify (in order to modify a block in the middle of the blockchain, all subsequent blocks have to be re-created).
There are two types of users in the blockchain system: users who add entries to the ledger; and managers who create new data blocks from those entries (a block may contain several entries) and validate data blocks structure against the rules. Depending on the type of managers, there are three types of blockchains:
- centralised services, where the ledger is managed by a single party;
- permissioned ledgers, where the distributed ledger is managed by an agreed-upon set of parties,
- permissionless ledger, where anyone could act as a manager.
Bitcoin

Bitcoin logo (source)
Bitcoin is a decentralised cryptocurrency and payment system created by Satoshi Nakamoto in 2009. In Bitcoin, all transactions are recorded in a public distributed ledger so anybody can track the balance of all Bitcoin account.
At the same time, the Bitcoin ledger itself does not contain the identities of its users. Accounts are identified by cryptographic pseudonyms -- users' public keys -- and one user may have several public key pairs. Users in the Bitcoin system do not have any physical or even digital coins; they only have technical means to prove that an account (and thus its balance) belongs to them. This is accomplished with private keys and digital signing.
In the following, we give a brief technical overview of Bitcoin transactions. Every user in the Bitcoin system has at least one key pair that consists of a public and a private key. The public key is used to generate the user's pseudonym, i.e. the account number and the private key is used to make transactions, i.e. transfer Bitcoins. A Bitcoin transaction is a digitally signed message stating who is the new owner of the specified amount of Bitcoins. The new owner is identified by their account number (public key), and the transaction is signed by the current holder of the Bitcoins. If the transaction is successful, the new owner is then able to spend these Bitcoins, and so on.
Next, users send their signed transactions to blockchain managers to commit them into the blockchain. To commit transactions into the blockchain, managers collect one or more transactions and add a new data block containing these transactions into the blockchain. However, adding a new block to the Bitcoin blockchain is computationally challenging as the new data block must conform to the specified rules: its SHA-256 hash must have the first n bits set to zero. As there is no efficient algorithm to generate such hash value, a brute-force method that uses a lot of computing power is used. A suitable hash is found by changing the value of a random number that is part of the data block. This process is called mining, as whoever manages to find a suitable random value and create a data block with a suitable hash value is awarded a certain number of Bitcoins. In addition, this miner gets to keep all of the transactions fees tied to transactions in this block, if any. The mining award halves every four years in Bitcoin blockchain and is currently 6.25 Bitcoins for creating a suitable block. The last halving happened in May 2020. Initially, Bitcoin mining was also possible using computer CPUs and graphic cards (GPUs). Now, mining requires so much computing power that special-purpose hardware is required, and managers form mining pools, where block creation awards are distributed between pool members.
The Bitcoin system has built-in controlled deflation as the maximum number of Bitcoins to ever exist is capped to 21 million. At the same time, mining becomes gradually more difficult as there are more and more miners and so finding a suitable hash value quick enough becomes a problem. This, in turn, means that Bitcoin transactions have become slower and more expensive. For example, in December 2017, committing a transaction took on average one hour, and the average transaction fee was about 10 dollars. Another possible problem with the Bitcoin system is that the mining resources are converging to China, and the system is only secure as long as no party controls more than half of the total mining resources. If this happens, it is possible for this party to start modifying old blocks in the blockchain, i.e. transaction history, although with great computational cost.
Above is a very general overview of the Bitcoin system. More technical details are in the Bitcoin protocol description.
Bitcoin and money laundering
Bitcoin is not designed to provide anonymous transactions. Still, it is not controlled by regulators, and everyone can join the system. Thus, Bitcoin has been a good way for criminals to transfer funds. All they had to do was to somehow obfuscate the origin of the received bitcoins to prevent detection. As you remember, all of the Bitcoin transactions are public; thus, all of the transactions done by the criminals are also public. However, the transactions are connected to a pseudonym, and this can protect their identity. But how can the criminals anonymously use the bitcoins to either buy something or to convert it to a mainstream currency?
One popular method is to use mixing services who receive bitcoins and randomly distribute the received bitcoins to multiple wallets. The services benefit from taking a small percentage of the transaction as a service fee. The clients of the service benefit as now their bitcoins are harder to trace, especially if the bitcoins are mixed multiple times. The mixing services could also be used by people who want to protect their privacy. Therefore, it is not only a service for the criminals, especially if considering that the mixing service itself might connect the sender pseudonym and the receiving pseudonym in certain situations (legal request). Similaly, if the mixing service is compromised, it not provide anonymity to its clients.
So why has Bitcoin been used by cybercriminals if it has a problem with anonymity? One of the reasons is that it is possible to automate much of the process, i.e., creating accounts, transactions and money laundering. Thus, it was possible to create new wallets for new ransomware victims dynamically. Once the ransomware targets paid the ransom, the corresponding wallets were automatically emptied and the bitcoins mixed. In addition, converting laundered bitcoins to US dollars or euros is easy as there are many exchanges. However, it was much more difficult to cash out less known cryptocurrencies. This has now changed, and thus also the cybercriminals have moved to use cryptocurrencies that are anonymised by design. The Bitcoin system is also more expensive to use as the transaction fees have gone up significantly, e.g., in January 2018, the transaction fee was over 30$. The fee fluctuates a lot, and one can not be certain how much it will be in a few months.
Ethereum

Ethereum logo (source)
The Ethereum blockchain was created in 2015 by Vitalik Buterin. Ethereum is also a cryptocurrency system, and the currency is named ether. In most cases, Ethereum started out as very similar to Blockchain but also had some notable differences. For example, mining new Ethereum blocks required one to find a suitable ethash value that is internally based on the Keccak (SHA-3) hash function. Ethash was designed to be resistant to hardware acceleration by requiring a lot of fast (and expensive) memory. This tried to mitigate one of Bitcoin's problems, where using special-purpose mining hardware makes mining difficult for the general population.
A blockchain that uses computationally intensive tasks (e.g. finding a suitable hash value with brute-force) to create new data blocks is said to use a proof of work method (in Estonian: töötõendus). The problem with proof of work is that it wastes a lot of energy, and therefore some blockchains have opted for an alternative method to create new data blocks: proof of stake (in Estonian: panusetõendus). In a proof of stake system, in order to add a new data block to the chain, managers must bid with their existing cryptocurrency (e.g. ether) for the right to do so. To avoid a block creation monopoly by the richest blockchain manager, the right to add a new block is granted by a lottery, where each manager's chance to win is proportional to their stake (bid). The manager, who wins the lottery, gets the right to add the new block by signing it with their private key. They also receive all of the involved transaction fees (if any) and the prize for adding the new block (if any), just like with mining and proof of work.
Ethereum transitioned to proof of stake consensus system on September 15, 2022 (see the Merge). Unfortunately, at the same time several forks of Ethereum were created that continue to use proof of work.
Smart contracts
Some blockchains (e.g. Ethereum) allow users to create smart contracts (in Estonian: lepingumonitor), i.e. program automated actions into the blockchain itself. In its simplest form, a smart contract is a "IF <condition> THEN <action>" type of statement, where a condition is something that blockchain managers can verify as they add new blocks to the chain (e.g. adding ether to some specific account) and action is something that the managers can execute (e.g. creating a new transaction to send a specified amount of ether to a specified account). As such, smart contracts are programs (contracts) that are executed (enforced) in a distributed fashion. In Ethereum, the Solidity programming language is used to create smart contracts.
One must be extra careful when creating smart contracts as they are immutable, i.e. they cannot be changed once they are published in the blockchain (given that modifying the contract is not built into the contract itself). Modifying or deleting a faulty smart contract would mean "rewinding" the blockchain that requires consensus among all of its managers (and possibly also users). Some of the most famous broken smart contracts include the DAO and the vulnerability in the Parity software.
Payment systems offered by the banks
Debit card
Wikipedia provides the following example of a debit card:

- Issuing bank logo
- EMV chip (optional)
- Hologram (may be on the back side)
- Card number
- Type / brand of the card
- Date of expiry
- Name of the cardholder
A debit card (i.e., the most commonly issued card) allows the cardholder to use the money from his/her bank account. Previously most of the debit cards functioned with the help of the magnetic stripe that is located on the back side of the card. As the information on the stripe was static, it was easy to copy. E.g., a device that allows reading the info from the stripe costs around $20. Thus, one had to give a signature while making a payment with such a debit card. Times have changed in many places around the world, and now a majority of issued cards contain an EMV chip in addition to the magnetic stripe. The chip contains a cryptographic key that can only be unlocked and used by entering a correct PIN code. Now banks assume that only the cardholder knows the PIN and thus is the only one who can use the card (at least in the payment terminals that only support chip-based cards). There are still some countries in South America and Asia where the magnetic stripe is still widespread. They are also used in the United States.
As it is trivial to clone the information on the magnetic stripe, then one should make sure that the card is always visible while the payment is made. Even if the card contains a chip, the information on the magnetic stripe could still be used for payments. You might be wondering why we need old technology when we already have chip-based cards, but the problem lays in assuring compatibility. There are still ATM machines and payment terminals that do not contain the technology to support chips based cards. In addition, some of the new ATM machines verify if the card contains valid information on the magnetic stripe. One more reason might have to do with the usability of the card, namely, when the chip is damaged, the magnetic stripe could be used as a replacement while making the payment. Thus, if the card would only support chip-based transactions, then in some situations, it would not work. From the security point of view, the previous info is not a good thing as you may still lose your money even if your card has a chip on it. Some banks disable the magnetic stripe by default, while some banks allow the cardholders to disable the magnetic stripe. Thus, the bank issuing the cards is the one who decides how magnetic stripes are handled.
An attacker who wants to use the copied magnetic stripe in an ATM also has to enter the correct PIN code. Thus, the attacker also has to copy the PIN code. Devices that both allow to copy the magnetic stripe and PIN code are called skimmers. They are usually attached to ATMs in a camouflaged manner. Therefore, it might be difficult to detect the device as it mimics some of the components of the ATM. If you want to read more about the skimmers, then we suggest following the blog of Brian Krebs.

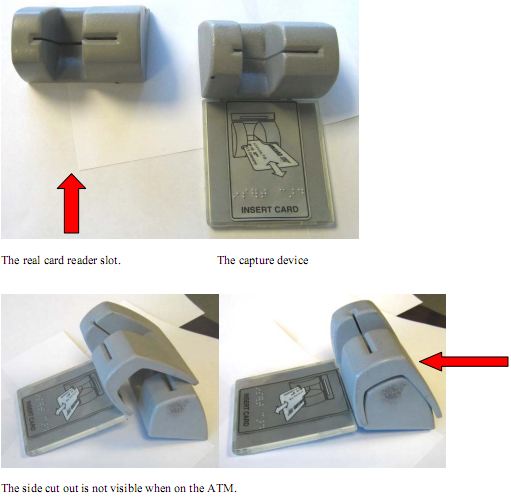
ATM with a skimmer. Source: A blog post by Brian Krebs
Debit plus
A Debit plus card is a debit card that has limited credit card functionalities. It can be used to make online payments like with a credit card. The payment process is similar to using a credit card; you will have to enter: your name (perhaps also the address), card number, date of expiry and the security code from the back side of the card.
When using a credit card, the transactions are done with the money that is loaned from the bank. However, by using a debit plus card, the transactions are done with the funds of the cardholder.
The legislation determines who is liable in case of the card is skimmed or when the card number leaks. Who has to prove the fraud - bank, service provider or the cardholder? The answer differs from country to country. In case the legislation is unclear, then it might be better to use a credit card as:
- credit card companies may give a faster refund
- some countries like the USA have special laws to protect against credit card fraud
- the right to dispute a transaction might expire later
- the burden of proof for showing liability may be on the card issuer
Leaks of credit card information are common as many online shops do not know how to properly secure the corresponding data. So, if the unfortunate happens to you, then you should approach your bank as soon as possible and dispute the transaction. What happens next depends on the local legislation, but for example, in Estonia, it could take a few months before a chargeback is made (if it is made at all).
In EU, the local legislation follows the EU directive: Directive (EU) 2015/2366 of the European Parliament and of the Council of 25 November 2015 on payment services in the internal market, amending Directives 2002/65/EC, 2009/110/EC and 2013/36/EU and Regulation (EU) No 1093/2010, and repealing Directive 2007/64/EC
Credit card
A credit card allows the cardholder to use loaned money that belongs to the bank. Such cards are required, for example, to do online payments, to book a hotel room, to rent a car.
The security of the credit card payment is rather low as one only needs to provide the credit card number plus the card security code in order to do online transactions (both are printed on the card itself). Sometimes the address of the cardholder is also required, but this is also a type of information that may be easily found online. Thus, it is important to protect the card itself both from getting into the wrong hands and also from cameras that may record the information printed on the card.
It gets worse as credit card information can be easily copied once it is used online. Therefore, the security level could be compared with the security level of plaintext passwords. If there is a merchant who does not properly secure the stored credit card information, the information can leak. One leak may be enough for an attacker to get all the information that is needed to do online transactions with the card. Thus, it may not be a good idea to use credit card in random online shops. While this might lower the probability of the illegal usage of the card, it is still possible that the larger and well known online shops also have security issues. Once your card number is maliciously used, you should dispute the transactions.
Usually, the cybercriminals are not using the stolen card numbers by themselves as laundering the money is a non-trivial task. It is easier for them to sell the collected information to third parties. The parties who buy credit card numbers may use them to somehow extract money from the card or to buy services like VPN in order to hide the monetary trace.
However, the security of using credit cards also depends on the legislation. For example, in EU the Payment Service Directive 2 (PSD2) makes it mandatory for payment service providers to use strong customer authentication (SCA). In essence, it mandates the usage of multi-factor authentication, which is a very effective way to prevent fraud.
Security
- Do not enter credit card information to a web site that uses HTTP.
- Do not enter credit card information to a web site that you do not trust.
- Think whether the service provider would have the means to securely store the credit card data. If the service provider can not be trusted and the purchase has to be made, then it is better to use a limited virtual credit card. However, not all banks offer the option to get a virtual credit card.
- Do not take a photo of your new fancy credit card and do not post it to social media :)
Near-Field Communication (NFC) Payments

Source: Wikimedia
NFC (near field communication) cards and payment terminals make it possible to do transactions without the card physically touching the terminal. The system contains an active party, which is the payment terminal and a passive party which is the NFC card. The terminal uses its electromagnetic induction to activate the antenna on the NFC card, which allows to communicate with the card. The card itself does not have a power supply and the range of the NFC card depends on the power source, i.e., on the design of the payment terminal. Thus, a large or a very large power source could be used to remotely activate the NFC card from greater distance.
As NFC cards can be used to do limited transactions as they can be used without providing the PIN code. The limit shows that the banks acknowledge that NFC cards have some security issues. If one wants to do a larger transaction then the chip has to be used with the PIN. However, if someone steals the NFC card then small payments could be made without authenticating the cardholder. Smartphone-based NFC payments are slightly different as in general they require the user to unlock the phone, which can be considered as authorising the transaction. There are a few exceptions, for example, it may be possible to buy transport tickets without authorising.
You can find more information about the security of NFC payments from the following paper: Security Analysis of Near-Field Communication (NFC) Payments.
Further reading
- Regular payment solutions
- Cryptocurrencies
- Once hailed as unhackable, blockchains are now getting hacked (2019)
- ISIS 'funded Sri Lanka Easter bombings with Bitcoin donations' (2019)
- Facebook's Libra cryptocurrency
- Bitcoin consumes 'more electricity than Argentina' (2021)

