Lab2: secure communication & privacy
Overview of the lab
One of the aims of this lab is to introduce the students to the real life usage of public key cryptography. We will try out tools that use end-to-end encryption for messaging and for synchronizing files between multiple computers.
For example, we will try using Signal Messenger as it provides one of the most secure implementations of end-to-end encryption while being easily usable. Signal is developed by cryptographers and is a non-commercial product. It has one other significant advantage compared to the other mainstream communication applications like WhatsApp, namely it is open source. This makes it possible for security researchers and for the community to audit the source code. The latter makes it possible to detect vulnerabilities and provides a guarantee that the application does not contain backdoors.
Setting up the lab environment
The lab tasks are designed to be solved in a virtual environment where all the tools are already installed. We are using Oracle VirtualBox to run a virtual machine, which contains the required tools. Both Oracle VirtualBox and the corresponding virtual machine are available in the computer classes of the DELTA building.
If you can not attend the lab and need to solve the lab tasks on your own, you can either manually install all of the required tools (recommended) or download the virtual machine, which we also use in the computer classes. In the latter case, you will also need to install Oracle VirtualBox along with its extension pack. NB! We are not able to provide support for installing software. This has to be done on your own in case you can not attend the lab. It should be much easier to solve the tasks if you install the required software on your own. If it is not possible to install the software or if the software does not function correctly in your machine, try to use the virtual machine. When coming across an issue while installing or using Oracle VirtualBox, first try to find an answer with the help of Google. In case that does not help you can post a description of the issue to the Moodle forum. However, in that case it will most likely be easier to install the required software manually, as getting Oracle VirtualBox to run may be tricky in some configurations (we can not provide such support over the internet).
Click here to read the instructions for configuring Oracle VirtualBox in the computer class.
1. How to view & edit EXIF data
Let's use exiftool to view EXIF metadata included in photos. The metadata can contain GPS coordinates, name of the photographer, and information about the camera that was used to take the photo.
Although, exiftool is designed to be used from the command line, it also supports drag and drop functionality. Thereby, it is possible to drag a photo into the exiftool window to display its metadata.
First, try to use exiftool. Navigate to the virtual machine desktop, open the folder exiftool-12.20, and start exiftool. After a few seconds a manual for the command line commands is displayed. In case you do not wish to use the command line, select the image that is of interest to you, select it with a mouse click, and drag and drop it on top of the file exiftool(-k).exe.

A black screen appears for a few seconds, after which the image metadata is displayed. You can use sample photos that contain GPS coordinates.

In addition to viewing metadata, exiftool also allows to remove either parts of the metadata or all of the metadata. However, this has to be done by using the command line. In case you are not afraid of the command line, try to remove metadata from an image. However, as an alternative you can use ExifCleaner, which is already installed in the virtual machine.
The command to remove all metadata is exiftool.exe -all= name_of_photo.jpg. However, in order to change the contents of the file, the name of the tool has to be renamed to exiftool.exe. As this task may seem complicated, you can also use ExifCleaner tool to remove image metadata. Once you have gotten used to exiftool and/or ExifCleaner, solve the following task.
Exiftool task and submission form
Download one image from the list of sample files and follow the instructions. (2p)
- Remove the metadata from this image.
- Use exiftool to check that the metadata was removed/cleaned.
- Edit the metadata according the following instructions.
- Right click the image and select Properties -> Details.
- Find the field with the label Author and enter your pseodunym for the information security course. You can find your pseudonym from the top right corner of this page by viewing your profile (this requires that you are logged in).
- Find the field with the label Title and enter your name.
- Click Apply and OK.
- Use exiftool to check that the metadata has been modified according to the instructions. If this is the case, submit the file as a solution.
2. TLS connection details
Find out how the TLS connection is setup between your browser and https://uttv.ee website. Check whether the server that is hosting uttv.ee website uses proper TLS configuration. In addition, find and read the certificate issued to uttv.ee.
TLS task (2p)
You are given a template_file.txt that you will have to fill with correct answers. Right click the link and select Save As. The file type must not be changed! The answers must be precise and follow the requirements as the grading is done automatically. The square brackets instruct which format to use when writing down the answers. The answers have to be written into the square brackets. For example, in case of [Number], we expect a numeric value and no other text. YYYY:MM:DD refers to year, month, and date, for example 2021:01:20. The slashes denote options out of which one has to be chosen. Strictly follow the instructions, do not write sentences to the solution file!
Find the following information:
- What is the common name of the certificate authority who issued the certificate for uttv.ee? [Name]
- When will the certificate expire? [YYYY:MM:DD]
- Which TLS version is negotiated and used between your browser and the server? [TLS1.1 / TLS1.2 / TLS1.3]
- Is forward secrecy used? [YES / NO]
- Which symmetric encryption algorithm is used to encrypt the communication? [Algorithm name]
- Which public key encryption algorithm is used to negotiate the session key? [Algorithm name]
- What is the length of the public key for uttv.ee? [Number]
- Which grade does https://www.ssllabs.com/ssltest/ assign to uttv.ee? [Letter]
Enter the following information to the template file and submit the file as a solution.
15. Lab 2: TLS & certificate info3. Syncing files with Syncthing
Syncthing is an open-source tool that allows to syncronise files between different computers. The file exchange is end-to-end encrypted between the connected devices. This is done with the help of TLS.
Find the icon for Syncthing from the desktop and start the program. A terminal window filled with text pops up. In case you scroll up you will see your new Syncthing ID that was just generated for you.

Let's try to understand what just happened and how the configuration was created. Navigate to C:\Users\Hacker\AppData\Local\Syncthing to view the keys and certificates. By default the certificates use the .pem file extension, which Windows is not able to read. But it can read .cer files that actually use the same internal format. So make a copy of cert.pem and rename it to cert.crt, then double click the file to view the certificate details.
With syncthing running, open its GUI by using a browser and navigating to 127.0.0.1:8384. In case it asks for anonymous usage reporting, select No.

Syncthing task (2p)
Your task is to connect to the lab supervisor's syncthing and create a shared folder.
First lets rename the name of our device in Syncthing as the device name is shown to the communication parties. To change the device name go to the upper right side of the Syncthing window and click on the button named "Actions". Once the menu appears, click on "Settings". Replace the device name with your name and click "Save".
Supervisor's syncthing ID is provided here:
- Kristjan's group: QJD2JEG-FA7NHLA-AY5ASQ3-DWQUQRB-2NM5S22-7KXOENJ-CAV7WEL-KVPHVAI
- Riivo's group: SEAHZMX-JMCCDQW-UAUXCIM-4UEVA4F-MXJXADX-B45OKPG-HO5X2Y2-HKMLDQ3
Copy the supervisor's syncthing ID and use it to create a connection. To do that click on the button that has the name "+Add Remote Device".

Now, fill in the required fields: Device ID and Device Name. You got supervisor's Device ID from the list above. You can choose yourself how to name the supervisor's device.

For the connection to be established the supervisor has to accept the connection request.

Once the connection has been established you should see a similar view to the one shown on the image below.

The next task is to create a new folder that can be shared. Each student creates a new shared folder by following the numbering of the lab computers. For example, the student sitting at computer 07 in computer class 2006 must create a shared folder with the name lab_07_2006 (in room 2029 the name would be lab_07_2029). Students who are doing this task on their own should use their pseudonym instead.
To share a folder click on the "+Add Folder" button and follow the aforementioned naming convention.

Now, share the newly created folder with supervisor's device. To do that click on the supervisor's device name on the list of remote devices and find the edit button. Click the edit button, find sharing tab, and the unshared folders. Mark the folder that you wanted to share.

Next, open the shared folder and create/place a text file into it. By clicking on the folder name in syncthing, you can see the folder path. For the virtual machines that we use in the lab, the path should be C:\Users\Hacker\name_of_shared_folder.

Now open this folder with file explorer. You can create a regular text file (.txt, not .docx) with Notepad. The name of the text file must be your pseudonym and the contents of the file must contain your name. In case connection is established between your syncthing and lab supervisor's syncthing, the file is transmitted and the supervisor can issue the points for this task.
Lab supervisor's syncthing must be online as otherwise it is not possible to establish connection. In case you are not able to connect after waiting a few minutes make a screenshot of the syncthing window. The screenshot must show the name of your shared folder and the short ID of supervisor's device. In case you were not able to share the file with the supervisor's device, submit the screenshot as a partial solution of this task.
Otherwise, if you succeeded, still make a screenshot of the syncthing window. Submit the screenshot of the browser window displaying a successfully shared folder as a solution.
16. Lab 2: Syncthing screenshot4. Overview of Signal
Signal is an open source messaging application that uses end-to-end encryption. It works on Android since version 4.0 and on iOS since version 9.0. Once Signal is activated on your phone you can also use a desktop client (it is supported on Windows, MacOS and on Debian based Linux distributions). You can get helpful information from Signal Messenger Basics and Signal Security.
It is not possible to use the desktop application without having Signal on the phone. This is due to the fact that Signal uses the phone number as an identifier of the user. This has also been one of the aspects of Signal that has gotten some criticism. At the same time, the developers of Signal are improving the protocol. For example, cryptographic methods help the Signal application to identify other Signal users who are in phone's contact list without revealing the contact list to Signal's servers. You can find more information about this method from the following blog post: Technology preview: Private contact discovery for Signal.


EFF has created helpful instructions for using Signal:
Signal task (1p)
Use Signal to send end-to-end encrypted messages. This is part of the second homework. If you are not able (or do not want) to try out Signal, then an alternative task regarding Signal is provided when you scroll down the page.
- Install Signal from Google Play / App Store.
- Signal uses contact list in order to find contacts. Therefore, you can see if anyone from your contact list is using Signal. We are using a prepaid card that is only used for the homework task and which has the following number:+372 five eight two seven three zero four six. You can add a new Signal contact directly from Signal. However, an alternative possibility is to add the number temporarily to your contact list.
- Now you are able to send messages to the test account. In case you have others Signal users in your contact list, you can communicate with them using end-to-end encrypted messages or calls.
- To claim the homework points send a hello message to the test account. The message must contain either your name or pseudonym from this course as otherwise it is not possible to assign points.
Alternative Signal task (1p)
If you are not able (or do not want) to try out Signal, then as an alternative you can solve the following task. It is possible to get up to one point from the Signal task. We will not give two points in case both the practical and the theory task are solved.
- Signal protocol is considered cryptographically secure but there are still ways to break the privacy of the sent messages. One trivial way is to hack the corresponding phone to get access before the message is even encrypted (this applies to any communication device / tool / software). It may also be possible to attack the method, which connects identities to the encryption keys. Read the following text and based on that explain briefly how the message privacy of Signal messages could be attacked and what is needed for that attack.
Using Signal in practice
In case you plan to start using Signal it may be useful to also have a desktop client. However, multiple security vulnerabilities have been found from the desktop implementation, which is build with the Electron framework. Thus, some people consider the desktop client less secure compared to the phone application.
In order to activate your account of the desktop client, it has to be connected with the Signal application on the phone. This can be done by opening the Signal application on the phone and scanning the QR-code that is displayed in the desktop application. The QR-code scanning functionality can be found from Signal's settings.
Signal may have less functionalities compared to the mainstream communication applications. One of the reasons is the lack of resources for adding functionalities but the other reason is the consideration of security. For example, it is non-trivial to synchronize messages across different devices as each Signal application has its own cryptographic keys and there are protective measures to protect the exchanged messages.
If you have reached this point, the mandatory practical tasks have been solved. However, we ask you to read the overview about the security of email exchange. That information may be included when creating the exam questions.
5. Securing email exchange
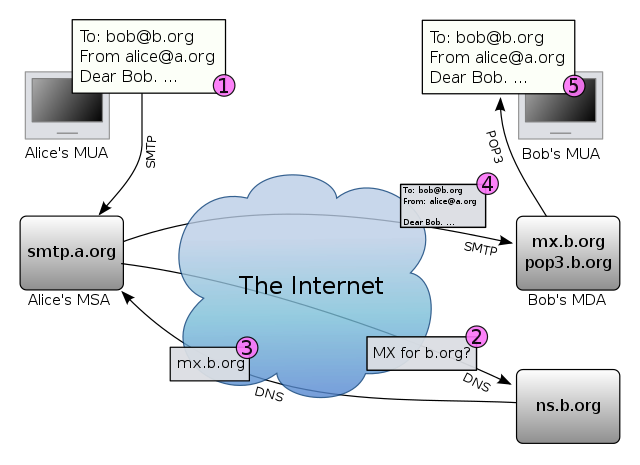
How email exchange works
Simple Mail Transfer Protocol (SMTP) is used to transmit emails both between the user and email server and between the mail servers. However, email client software is commonly configured to use SMTP only for sending emails. In order to receive emails client software uses either IMAP or POP3.
IMAP protocol is commonly used nowadays as it provides support for multiple simultaneous clients. Therefore, with IMAP it is possible to view emails in both the smartphone and in a laptop without the emails being deleted from the server. However, POP3 is an older protocol that first fetches the mail and then deletes it from the server which means that by default mail can be downloaded to a single device.
One might wonder if SMTP, IMAP and POP3 always encrypt the email traffic in order to protect confidential information from leaking. Actually, all of these protocols support the transmission of data over SSL / TLS but this is an optional feature. Special ports are reserved for these protocols to transmit data over SSL / TLS. Secure SMTP is called SMTPS and it uses port 465. Secure IMAP is called IMAPS and it uses port 993. Secure POP3 is called POP3S and it uses port 995. It is obvious that the extra S in the abbreviations stands for secure and it just means that the protocol is used inside of a SSL / TLS session. Most email servers support the secure versions of these protocols but the user may have to configure the email client software to use the correct port.
There is a feature that enables encryption even for the plain SMTP, IMAP, POP3 and this feature is called STARTTLS. STARTTLS adds SSL / TLS by default if the corresponding mail server supports this. Most well known email providers have enabled support for STARTTLS. However, if a mail server does not support STARTTLS, then the user will have to configure the email client software to use a port that provides an encrypted connection.
Security and privacy issues of email exchange
The protocols that are used to exchange emails are not designed to take security and privacy seriously. These protocols were designed to get the job done in an environment where security was not so relevant. However, these protocols are still alive and it is difficult to modify them or to replace them with more secure protocols.
By default email is not encrypted, some links between the mail servers might be encrypted but this does not mean that the content of the email can not be intercepted, read and modified. It might be possible to encrypt the links between the mail clients and mail servers but while the mail is routed through the Internet it might pass servers that do not support encryption. In addition, as the content of the mail is not end-to-end encrypted, the mail servers are able to read the contents of the emails.
Some SMTP servers support STARTTLS which enables to automatically switch from an unencrypted connection to an encrypted connection over SSL / TLS. However, STARTTLS is mostly supported by the major email providers and many servers still do not provide this option. When STARTTLS is not available and the mail client is not forced to use a secure mail exchange protocol then the email is exchanged in plaintext, i.e., in an unencrypted form.
A message transfer agent (MTA) is used to relay emails from one mail server to another. MTA uses SMTP and deals with receiving messages and relaying messages. It is important to note that MTA-s do not have to communicate with each other over TLS/SSL. If one of the MTA-s does not support TLS/SSL then the email is exchanged in plaintext. In case an email is sent to a mail server that does not support TLS/SSL then it is guaranteed that the email will be transmitted in plaintext at least in one transmission step. Therefore, STARTTLS and secure mail exchange protocols do not provide confidentiality during the transmission of the email as one of the mail servers might not support TLS/SSL. Even when all links during the transmission of the email are secured by encryption the contents of the email can leak as the mail servers are able to read the email in plaintext. Therefore, one needs to trust the MTA-s while sending emails but this is not a very wise thing to do when the contents of the emails are confidential.
In addition, it is important to notice that the metadata in the header of the email can not be encrypted as this information is required for relaying the emails. Therefore, it is possible to intercept the metadata that contains: sender email address, recipient email address, sender IP, recipient IP, date, time, title of the email. This data is public and the mail exchange protocols do not provide means to protect such information.
Risks that are related with email communication:
- the contents of the emails can be intercepted and saved
- the contents of the emails can be modified
- the contents of the emails can become public information
- it might be possible to use someone else's identify
A very good overview of the security issues of email is given by the article Neither Snow Nor Rain Nor MITM ... An Empirical Analysis of Email Delivery Security (2015). It is written by researchers from University of Michigan, Google, University of Illinois.
Solution for the privacy and security issues
There is no ideal solution for the described security and privacy issues. The best available solutions use end-to-end encryption but they are not widely used. In end-to-end encryption the message is encrypted in the sender's computer and decrypted in the recipient's computer, which means that the intercepting party can not get access to the contents of the message. End-to-end encryption of emails is provided by PGP/GPG and S/MIME. As an alternative, it is possible to use other communication means that provide end-to-end encryption. One popular alternative used to be Off-the-Record Messaging (OTR) but nowadays Signal is considered to be one of the most secure communication applications.
Once you have finished reading the following theory part, you can attempt to solve the bonus task by using PGP/GPG to encrypt and sign emails.
S/MIME
S/MIME (Secure/Multipurpose Internet Mail Extensions) is a mail exchange standard that is based on public key infrastructure. In addition to providing confidentiality by using encryption, non-repudiation by using signing, it also provides authentication and message integrity. Similarly to HTTPS, each end user should have a key pair and a certificate that binds the identity (email address) with the corresponding public key. The certificate has to be signed by a trusted certificate authority (CA).
In order to encrypt emails with S/MIME one would need to have the public key of the email recipient. Usually the public key can be accessed if the recipient has previously sent a signed email which contains the certificate and therefore also the public key.
S/MIME is supported by several mail clients but it is rarely used as one would have to get a certificate that is signed by a CA. However, S/MIME is widely used in Estonia as each ID-card owner has a certificate signed by a CA. It is possible to send encrypted and signed emails using the Estonian ID-card. In order to do that one would have to search for the corresponding certificate and then use the email address that is in that certificate. The email addresses in the ID-card certificates are of the following format: Surname.Lastname[.X]@eesti.ee.
PGP and GPG
Pretty Good Privacy (PGP) is a computer program that was created in 1991. It allows to encrypt and sign documents and emails. Similarly to S/MIME PGP is based on public key cryptography. Each PGP user has a key pair but it differs from S/MIME by the way how keys are managed. PGP is not centralized, i.e., it does not use public key infrastructure. Therefore, one does not have to get a CA to sign a certificate which makes it easier to start using PGP.
Instead of using public key infrastructure where trust relationships are created between CA-s, PGP uses something that is called a web of trust. In the web of trust everyone can choose how much trust is given out and then the decision is bound by signing the corresponding certificate. If many people enforce the trust by signing other peoples certificates then a social network of trust is created where trust is a transitive relation as shown on the following figure.
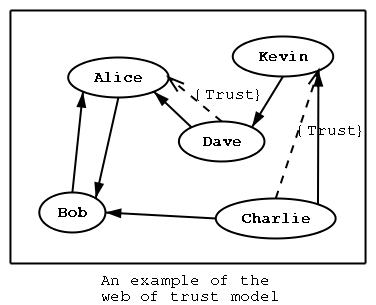
PGP trust relations. An ordinary arrow denotes that a certificate has been signed and the dotted arrow denotes a trust relationship. For example, as Dave trusts Alice and Alice has signed the certificate of Bob, then by the transitive relation Dave also trusts Bob, i.e., Dave believes that the corresponding public key really belongs to Bob. (Source)
Key servers are used to manage the trust relationships. One can download a certificate from the key server and also upload new signed certificates to the key server. Therefore, everyone can create new trust relations and publish them in the key servers.
Actually, PGP is an old commercial software product and therefore it is not used anymore. A standard called OpenPGP was created based on PGP in order to make the functionalities provided by PGP widespread. OpenPGP is supported by different software products which makes them interoperable. The most common and widespread software that follows the OpenPGP standard is GNU Privacy Guard (GnuPG or GPG). GPG is an open-source program that is available for free.
GNU Privacy Guard (GPG)
GPG allows to exchange emails and attached files in a secure manner. GPG allows to encrypt and sign emails which means that a third party is not able to secretly modify or read the contents of the emails. In addition, when an email is signed the the receiver can be sure who sent the email (actually, the receiver only knows that the sender had access to the corresponding private key).
GPG is considered to be one of the safest methods for encrypting data. However, GPG is not very popular and only a small group of people communicate by using GPG. Therefore, one can usually start using GPG only if the receiving party is instructed on how to setup GPG. There might be a situation when someone, e.g. a client, wants to submit confidential information and GPG provides a solution for this problem. Estonian citizens can use the encryption and signing functionalities provided by the ID-card but if the client is a foreigner then ID-card may not be an option. In such cases one could create an OpenPGP key pair for himself / herself or for the company. However, just creating the key pair is not enough, the key pair would also have to be published so that the clients could find the key. One option is to publish the key in addition to the key servers also to the company website in case the website is configured to use HTTPS.
The simplest way to use PGP is to run Thunderbird. Mozilla Thunderbird is a popular free and open-source email client that is developed by Mozilla Foundation. PGP is integrated into Thunderbird since version 78. If you want to read more about using PGP in Thunderbird, read the following instructions: https://support.mozilla.org/en-US/kb/openpgp-thunderbird-howto-and-faq.
Finishing the lab - remove the virtual machine
In case you were able to successfully complete the PGP task, you can close and remove the virtual machine. However, if you installed the virtual machine to your own computer, it would be good to wait for the instructors confirmation that the email was received before removing the virtual machine.
- Close the virtual machine: open the Start menu and select "Power" -> "Shut down".

- Next, remove the previously imported virtual machine from the main VirtualBoxi window. To do that, right click on the name of the virtual machine and select "Remove...".

From the dialog window select "Delete all files".

- Finally, make sure that you log out of the lab computer. We will give minus points to the students who leave the computer class without logging out from their accounts.
- In case you are solving the tasks on your own computer, you can now also remove the .ova file from your own computer (the file, which you used to import the virtual machine).